What are the hidden costs of maintaining legacy systems?
Due to the nature of legacy applications, it can be tough to argue change is necessary. They begin to feel like part of the furniture. But their impact can be damaging, even if it isn't obvious. Learn how to identify the impact of legacy applications, and what to do about it.
Published:
Last updated:
Finding it hard to keep up with this fast-paced industry?
Key takeaways:
________________________________________________________________________________________________________________________
Consider this scenario: a malicious foreign actor seeks to gain access to a large enterprise’s data and systems. Rather than the more common and increasingly sophisticated approach of a phishing attack on team members, the outsider discovers an easier path. The organization, like many, has a legacy system problem.
By compromising a legacy, non-production test account and using this to gain a foothold, cyber attackers can gain access to a small percentage of corporate email accounts, including those of members of the executive team and cybersecurity, legal, and other functions, exfiltrating emails and documents.
While this may sound like a hapless organization with poor IT practices getting its comeuppance, this is the story of the “Midnight Blizzard” attack on Microsoft in 2024, where the upper management of one of the most sophisticated technology companies in the world fell victim to this common vulnerability. Legacy systems are that big a threat.
If your organization has a legacy system problem, a damaging hack isn’t the only issue you should consider. The cost of ownership is more than modern equivalents in terms of ongoing maintenance, loss of efficiency, loss of productivity, and opportunity cost. Outdated systems also contribute to employee churn.
By migrating to a modern solution underscored by a cloud strategy, you can reduce the risk of these obvious (and hidden) threats across the business.

The financial burden of legacy systems
IT budgets are getting eaten up by legacy application costs, money that could be used somewhere else or for IT transformation. Unlike the data breach risk, these costs are not theoretical; they are being incurred by any organization with legacy applications.
According to Gartner, by 2025, companies will spend 40% of their IT budgets on maintaining technical debt. While technical debt goes beyond legacy applications, application costs can make up to 80% of the entire IT budget, and retiring legacy applications can lead to substantial cost savings.
Plus, consider the case for doing nothing: maintaining legacy apps leads to increasing costs for support and maintenance over time. In 2019, the US Federal government spent 80% of the IT budget on operations and maintenance.
This spending mainly included aging legacy systems, which posed efficiency, mission, and cyber risk issues. To put that into context, only 20%of the IT funding was assigned to development, modernization, and enhancement.
The direct costs of maintaining legacy on IT budgets
Let’s start by taking a look at some of the direct costs common with legacy systems.
1. Maintenance costs
Legacy applications require a lot of help to continue operating optimally. This maintenance can take the form of:
- Patching, especially security patches.
- Customizations and integrations to ensure disparate systems can interoperate.
- Specialist technical support for applications that require old code.
- Operational downtime when issues need to be fixed.
The average cost of operating and maintaining one legacy system is $30M, and by conservative calculations, at least $1.14 trillion is spent on the ongoing maintenance of existing IT investments.
2. Hardware and software upgrades
Hardware and software associated with legacy systems need to be upgraded regularly. This involves pumping money into technology that may not have a future outside a specific use case and doesn’t drive value for the business. It’s simply a band-aid for a solution past its sell-by date.
Hardware upgrades are more costly as specialized machines and components are required, and sourcing them becomes harder as suppliers with compatible tech dry up.
Three-quarters of IT teams managing legacy systems spend up to 25 hours a week on patch management. These recurring costs and productivity losses have a material impact on the bottom line. The only way to escape the never-ending cycle of legacy system costs is through digital transformation.
3. Licensing fees
Delaying migration can lead to spiraling licensing costs. In 2015, the Royal Navy forked out $9 million to continue using Windows XP after stating its legacy programs were reliant on older Windows products.
Trying to ensure continuity can force companies to double down on complex, special licensing arrangements. Inevitably, these fees soar as vendors prioritize support for newer systems and charge more to offset the resources invested in maintaining outdated software.
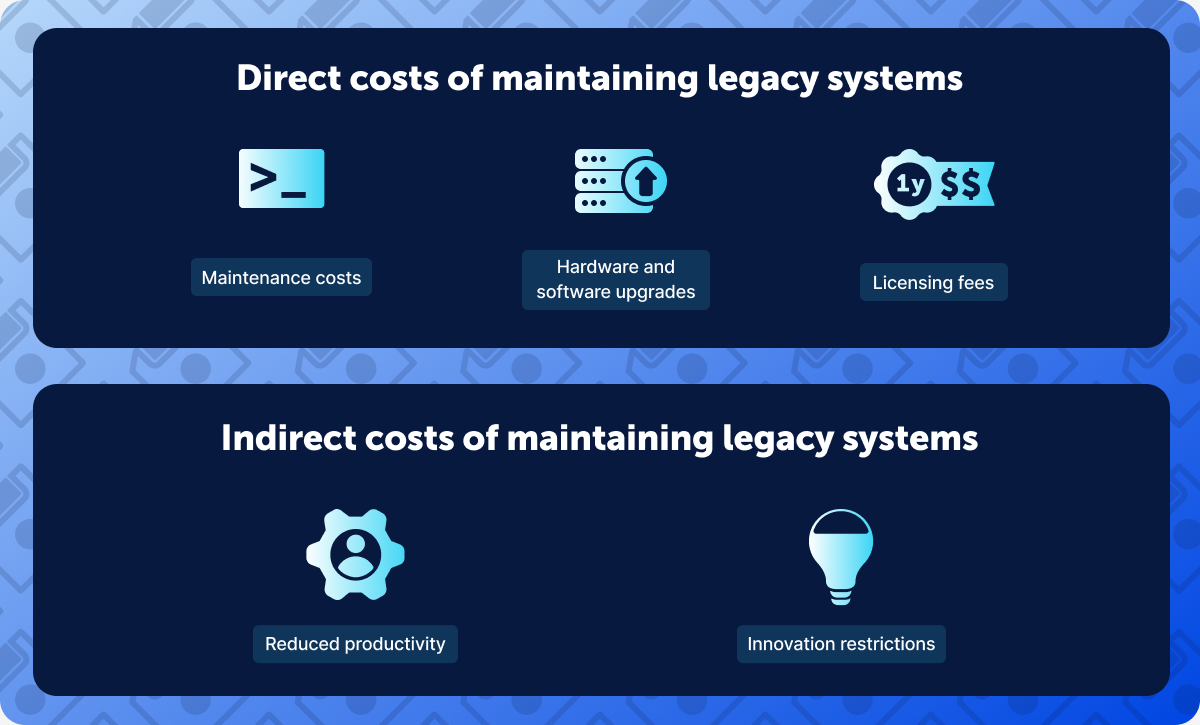
The indirect costs of maintaining legacy on IT budgets
Let’s explore some of legacy systems' specific indirect costs and how this can impact a business team.
1. Inefficiencies act as a drag on productivity
Slow, inefficient legacy applications lower productivity, impacting overall business performance. In studies in the UK, 48% of the study population wasted three hours or more per day due to inefficient systems, which over a year cost the average UK business at least £28,000. Forcing your staff to develop workarounds or waste time waiting for processes to complete is not a recipe for an agile, innovative organization.
A Total Economic Forum study by Forrester showed that retiring old legacy systems could reduce hardware and operational running costs by 65%. This is to say nothing of the gains in efficiency, scalability, and agility through strategic application alignment with modern IT environments.
2. Opportunity costs
Organizations that spend time and money wrangling legacy applications are missing other opportunities to innovate and grow.
90% of IT decision-makers say legacy systems are holding their organizations back from using digital technologies to innovate or make operational efficiencies. Modernizing legacy applications can liberate organizations from these constraints, freeing up time and money for more strategic initiatives.
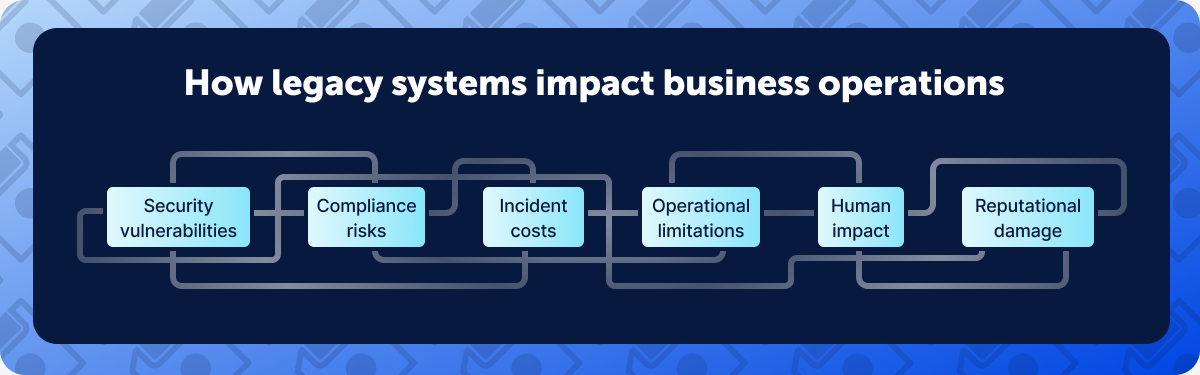
The impact on business operations
The total cost of maintaining legacy software and systems is difficult to quantify. The effects are far-reaching, impacting everything from employees at their desks to security operations and competitiveness in international markets.
Let’s explore some of the many associated costs and operational risks of legacy systems.
1. Increased security vulnerability
Unpatched vulnerabilities may be the biggest enterprise cyber risk. Outdated security and lack of updates make legacy apps prime targets for cyber threats, as attackers actively exploit these blindspots and target unpatched end-of-life (EOL) and legacy systems.
As the Microsoft example illustrates, many bad actors unsurprisingly target vulnerable, overlooked systems to gain initial access to target systems. In its study of critical federal government systems, GAO noted that several legacy systems were operating with known security vulnerabilities and unsupported hardware and software.
Businesses with legacy vulnerabilities face a more varied (and dangerous) threat landscape, which increases vulnerability management costs. Application modernization is the solution here, allowing security teams to combat growing threats with the best available security tools.
2. Compliance risks
Outdated technology can impair your ability to comply with regulations, increasing your compliance risk.
Legacy systems’ lack of compliance with stringent data privacy laws like the General Data Protection Act (GDPR), the California Consumer Privacy Act (CCPA), or the Health Insurance Portability and Accountability Act (HIPAA) complicate the management and protection of sensitive customer data.
A study from the Capgemini Research Institute found that when executives were asked to rate the top challenges organizations face while preparing for the CCPA, legacy IT (42%) emerged as critical.
Companies that fail to meet these obligations could face penalties and steep fines. In fact, violations of GDPR alone cost companies over $2 billion in 2023. As state-level privacy regulations continue to be enacted, this concern will only grow more relevant in the future.
3. Incident costs
Legacy systems often lack current oversight, leaving you unaware of stored ROT, duplicates, and sensitive data at risk. This can lead to significant dangers like breaches, data loss, or regulatory issues. Proactive measures are a must: data minimization and defensible disposal will shield at-risk data in the event of a breach or cyber attack.
In addition to the Microsoft example mentioned above, there have been many examples of outdated or unpatched technology causing major data breaches. The Equifax data breach in 2017, which exposed the personal information of approximately 147 million people, was attributed to a failure to patch a known vulnerability in the Apache Struts framework, which was a part of their legacy system. In 2017, the WannaCry ransomware attack affected numerous organizations around the world, including the UK’s National Health Service, by exploiting a vulnerability in an unpatched version of Microsoft Windows.
In 2020-2021, the Accellion file transfer appliance, considered legacy software by the company itself, was exploited, affecting multiple organizations and exposing sensitive data.
A series of breaches at customers around the world began in late 2020 and continued into early 2021. The company had already been moving customers off the appliance, planned to end support for the appliance in April 2021, and discontinued support for its operating system in November 2020.
4. Operational limitations
Legacy systems hold companies back. Rather than being proactive and adapting to rapidly changing market demands and regulatory shifts, many have to work around the deficiencies of an infrastructure no longer fit for purpose.
It can stunt growth and expansion: a lack of flexibility and scalability makes handling growing data volumes and new processes incredibly challenging, while slow performance, security risks and ballooning maintenance costs weigh down departments and cause major issues, inefficiencies and delays in daily operations.
Employees also have to work within the constraints of outdated software and hardware. In an age of hybrid working, a lack of cloud-based features and remote access, for example, hinders productivity and prevents real-time collaboration. Incompatibility with newer devices and operating systems also creates bottlenecks and silos within the business.
5. Human impact
It’s not just structures and processes that suffer; legacy tech also takes its toll on humans: employees, management, and customers. Wrestling with slow and outdated systems breeds frustration and dissatisfaction, which increases stress and affects morale.
Legacy systems offer a poor user experience and work against employees, making it painful to get jobs done. In the long term, burnout loosens the bonds between employees and the company, leading to higher turnover and skilled employees leaving for enterprises with modern, efficient systems.
Even those who remain committed miss important development opportunities, as they are forced to firefight and troubleshoot rather than learn skills for new technologies.
This limits professional advancement and stunts career growth. Soon, companies with an outdated infrastructure and culture develop a reputation for being laggards rather than innovators, making it difficult to attract new talent.
6. Reputational damage
While data breaches and system failures are becoming more common, each one is still devastating for the victim in terms of customer trust and reputation. Customers trust organizations to treat their data carefully and can rightly feel betrayed when a data breach occurs and it becomes clear that the organization mishandled their data.
Along with eroding customer trust, data breaches caused by an outdated system can lead to significant reputational damage for the victim.
United States mobile service provider T-Mobile has fallen victim to nine data breaches in the period between 2018 and 2023. Each of these breaches, no matter the size, impacts the company’s brand image, further painting the company as one which does not properly safeguard customer data.
In 2018, hotel conglomerate Marriott International discovered that attackers had compromised its reservation system, gaining access to information from 500 million guest records, exposing the personal information of hundreds of millions of individual guests from around the world.
The cause of the breach stemmed from legacy systems that were part of the company’s 2016 acquisition of Starwood, showing the importance of cybersecurity during mergers and acquisitions (M&As).
In addition to a more than 5% drop in its share price, the company was also hit with an £18.4 million GDPR fine for failing to secure millions of guests’ personal details, further damaging Marriott’s brand.
Making the case for modernization
One of the issues with legacy applications is that senior leadership can be blind to their everyday issues, risks, and hidden costs. Obtaining buy-in for migration or application retirement can be challenging, and it may represent a seemingly significant capital expenditure to maintain the status quo.
It’s important not to fall prey to the sunk cost fallacy. Just because you’ve invested time and money into a system, you don’t have to stick with that system indefinitely.
Benefits of migration or application retirement
In many organizations, senior leadership views IT primarily as a cost center and may be focused on limiting operational expenditures. This short-term thinking can lead to poor decisions that harm security and compliance. In addition, money spent on legacy applications is money that, by definition, is not going to innovation.
Cost-benefit analysis
When making the argument to retire a legacy application, it is important to include all the ongoing costs rather than the obvious licensing or subscription costs. We need to compare apples to apples, so ensure you record all the costs of a legacy application. These hidden costs may include:
- The amount of time your staff spends fielding support inquiries or resolving issues.
- Development or maintenance of custom integrations or interfaces.
- Workarounds deployed to overcome the shortcomings of the legacy application.
Use specific examples or figures from your organization; otherwise, quote the numbers mentioned earlier in this piece. It is highly unlikely that your organization is immune from these trends. That’s why it's important to make sure this point is not lost on your executive team or board.
To make this process easier, we have created a calculator that allows you to estimate the cost of decommissioning legacy applications.
Strategies for minimizing costs
A modernization project can be complex, but there are effective strategies you can implement to reduce the true costs of updating hardware and software.
- Prioritize modernization: Identify critical legacy systems based on their business impact tech stack, performance, security threats, and business needs. Then, prioritize replacing those that will yield the best operational and financial benefits.
- Optimize maintenance: Conduct regular performance assessments and schedule daily or weekly maintenance checks to reduce costly disruptions and extended downtime.
- Consider outsourcing: Evaluate whether you can source expert help from third parties to complete tasks such as data migration. Outsourcing specific tasks or functions will reduce the burden on in-house teams and enable you to leverage specialized tools and resources.
- Explore cloud migration: Consider migrating legacy systems to the cloud using Microsoft Azure to reduce infrastructure costs and improve scalability. You don’t need to greenlight a full system replacement overnight. Adopt a staggered approach to spread costs and migrate at your own pace.
The future of legacy systems
Legacy systems cannot be rebuilt overnight, and they shouldn’t be. A careful, strategic, and phased approach to modernization can, slowly but surely, bring tech out of the darkness and into the light.
Cloud computing and artificial intelligence (AI) have made the process more viable, giving organizations the tools to migrate without the hefty upfront investment required to overhaul on-premise infrastructure. Once the cloud infrastructure is established, you can adopt a hybrid IT model (in the short term) as part of a gradual transition, offloading viable workloads to optimize costs and enhance scalability.
AI automation and machine learning can analyze patterns and flag issues to streamline tasks and address modern technology challenges during the transition. You can automate:
- Data migration: Automate the transfer of data between systems.
- Security and compliance: Use new security features and automated patches and checks to ensure consistency across both environments.
- Application deployment: Rather than manually deploying applications, use CI/CD pipelines to automate the process.
- Backup and disaster recovery: Automate backups to protect data and minimize downtimes during the migration.
Summing up
Legacy systems represent a significant cybersecurity risk to every organization and an ongoing drag on efficiency, costs, and productivity. Organizations of all sizes, from small businesses to technology leaders like Microsoft, suffer from problems with legacy applications, which are exacerbated by wider technical debt issues.
Due to the nature of legacy applications, it can be tough to argue that change is necessary. Legacy systems’ licensing costs are predictable, and the impact on productivity and efficiency can go unnoticed.
The systems begin to feel like a part of the furniture. However, modernization and legacy application retirement are crucial to improving security, compliance, and productivity as well as reducing risk and overall cost.
Now, it is time to assess your systems so you can chart your path to modernization. Learn more about how decommissioning legacy applications is the next step to reducing your IT budget and enhancing innovation.
💸 See how much legacy applications are costing you with our application retirement calculator.
FAQs
What are the common signs that a system has become a legacy system?
Legacy systems are defined as old or outdated software or hardware that is still in use but lacks features or functionality found in modern systems. Common indicators of a legacy system include incompatibility with newer technologies and a lack of support from the vendor (feature and security updates, etc.).
This can result in tangible consequences for a business: slow performance, frequent outages, poor customer experiences, high maintenance costs, and security breaches.
If a system no longer meets business requirements and is a drag on compliance efforts, it’s likely a legacy system.
What are some common challenges in modernizing legacy systems?
Two-thirds of CTOs say complex dependencies within legacy software and accumulated technical debt from legacy code are the biggest challenges with modernizing legacy systems. Over time, IT teams patch or modify existing systems rather than redesign them to address security vulnerabilities, making it more challenging to “untangle” and integrate with new systems.
Other challenges include data migration, budget and time constraints, skill gap issues in the workforce, and potential downtime during the transition.
To overcome these issues, you must:
- Conduct a system audit and create a roadmap for modernization.
- Prioritize critical dependencies and use a phased approach to minimize disruptions and costs.
- Upskill and onboard team members in relevant technologies.
- Engage stakeholders to align modernization goals with business objectives.
- Prioritize compliance to ensure a new system meets stringent security and regulatory standards.
How can I justify the cost of modernizing legacy systems to my organization's leadership?
It’s best to frame modernization as a strategic investment. You must present data and evidence to leaders that the costs of maintaining legacy systems are unsustainable and that transitioning away from them will mitigate risks, increase efficiency, and drive growth.
To support your case, develop a clear ROI case and link modernization to current business goals.
Discover Connectors
View our expanded range of available Connectors, including popular SaaS platforms, such as Salesforce, Workday, Zendesk, SAP, and many more.


